Anthropic just dropped a quiet announcement with a very loud implication: Claude Code Security, a new capability built into Claude Code on the web, now in a limited research preview. It scans codebases for security vulnerabilities and suggests targeted patches for human review—with a multi-stage verification flow designed to reduce false positives and keep humans in control.
That’s the “product” part. The “oh…” part is the research behind it.
Anthropic says its Frontier Red Team, using Claude Opus 4.6, has already found and validated more than 500 high-severity vulnerabilities in real, production open-source codebases—including bugs that had gone undetected for decades.
And Wall Street reacted as if somebody had just hinted that a chunk of the cybersecurity industry’s subscription revenue might be… optional.
Within hours, multiple cybersecurity names sold off sharply. A Bloomberg report described declines including CrowdStrike (-8%), Cloudflare (-8.1%), Zscaler (-5.5%), SailPoint (-9.4%), Okta (-9.2%), and the Global X Cybersecurity ETF (-4.9%) (closing at its lowest level since November 2023).
You’ve probably seen the spiciest version of the story circulating online: “Anthropic ended cybersecurity subscriptions” and “$10B wiped out in an hour.”
Let’s slow down and separate what’s verified from what’s vibes.
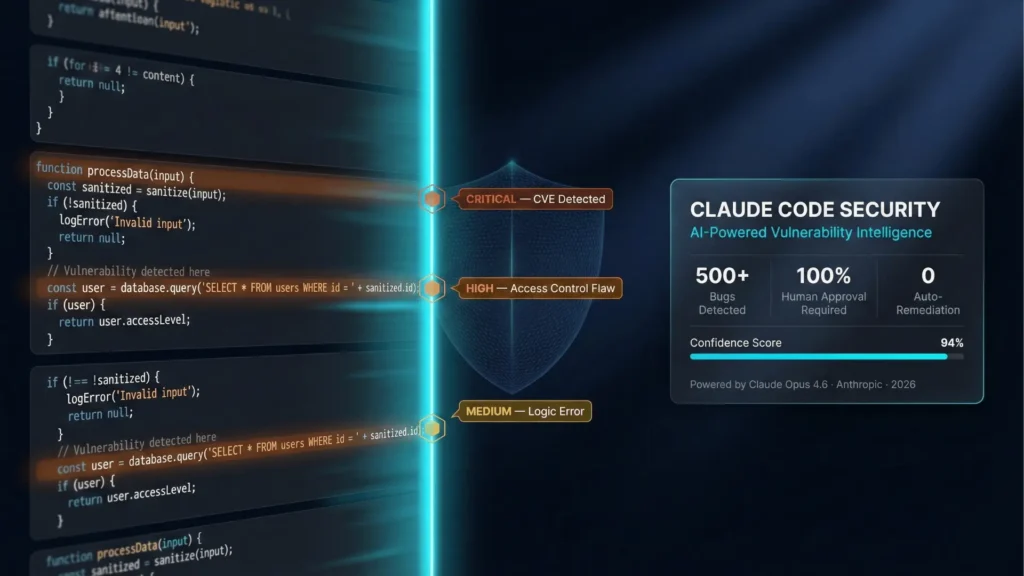
What Anthropic Actually Announced
Anthropic’s announcement is straightforward:
- Claude Code Security is built into Claude Code on the web.
- It’s available in a limited research preview (not a broad GA rollout).
- It scans codebases for vulnerabilities and suggests targeted software patches for human review.
- Every finding goes through a multi-stage verification process: Claude “re-examines” results and tries to prove/disprove its own findings to filter false positives; it also assigns severity ratings and provides a confidence rating.
- Nothing is applied without human approval. Claude suggests; developers decide.
- Preview access is aimed at Enterprise and Team customers, with free expedited access encouraged for open-source maintainers.
Fortune’s reporting aligns with that framing and adds one key nuance: it describes Claude Code Security as Anthropic’s first product aimed at using AI models to help security teams keep up with the volume of software bugs, while emphasizing that it doesn’t apply fixes automatically and developers must approve changes.
So yes: it’s a product capability. But it’s being released cautiously—as a research preview—because of the obvious dual-use risk: the same capability that helps defenders can help attackers.
The Core Claim That Lit the Fuse: “500+ High-Severity Vulnerabilities”
Anthropic is not being coy about the headline research result.
In its announcement, it says that using Claude Opus 4.6, its team found over 500 vulnerabilities in production open-source codebases—bugs that had gone undetected for decades—while working through triage and responsible disclosure with maintainers.
On Anthropic’s red-team site, the “0-Days” write-up states:
- They’ve found and validated more than 500 high-severity vulnerabilities.
- They’ve begun reporting them, initial patches are landing, and they’re continuing to work with maintainers.
That’s not “Claude caught a few issues.” That’s “Claude is now operating as a vulnerability discovery engine at industrial scale”—and doing it in the kinds of messy, sprawling code that real systems depend on.
Fortune also reports that Opus 4.6 found vulnerabilities “undetected for decades,” and notably claims it did so without task-specific tooling, custom scaffolding, or specialized prompting in testing of open-source software used across enterprise systems and critical infrastructure.
This is the part that matters: if a model can reliably find novel, high-severity vulnerabilities—not just pattern-match known issues—then “security review” changes shape. Less like “needle-in-haystack detective work.” More like “automated triage + human judgment + fast patch cycles.”
Why This Isn’t “Just Another Scanner”
Anthropic contrasts Claude Code Security with traditional rule-based static analysis:
- Static analysis tools typically match code against known patterns, catching things like exposed passwords or outdated encryption, but often missing more complex vulnerabilities like business logic flaws and broken access control.
- Claude Code Security is presented as reading code “like a human researcher,” tracing how components interact and how data moves through the application.
That difference—pattern matching vs contextual reasoning across a codebase—is exactly where the market’s fear comes from. Rule-based tools are useful, but they’re limited by the rulebook. Humans can reason outside it, but humans don’t scale.
Anthropic’s pitch is: “What if you had more humans… without hiring more humans?”
Not in the dystopian sense. In the boring, operational sense: backlogs shrink, triage becomes faster, and critical bugs get caught earlier.
“It Found Bugs Humans Missed for Decades.” How?
This is where Anthropic’s red-team write-up matters, because it gives a concrete look at how the model is being used and how findings are validated.
The Setup (and Why It Matters)
Anthropic says it put Claude in a “virtual machine” with access to the latest versions of open-source projects and standard utilities—and it had access to vulnerability analysis tools like debuggers or fuzzers. Crucially, they say they didn’t provide special instructions or a custom harness that would “teach” it how to find vulnerabilities in those projects.
They also directly address a real pain point for maintainers: hallucinated bugs. They say they validated every bug extensively before reporting, focusing initially on memory corruption vulnerabilities because they’re easier to validate reliably (crashes, sanitizers, etc.).
That validation step is not a footnote. It’s the difference between:
- “AI is spamming maintainers with nonsense,” and
- “AI is producing actionable, verifiable reports that get patched.”
Anthropic also notes that as volume grew, they brought in external human security researchers to help with validation and patch development, explicitly optimizing for reducing false positives and meaningfully assisting maintainers.

Three Examples (Ghostscript, OpenSC, CGIF)
Anthropic shares examples of vulnerabilities Claude found that were later patched by maintainers.
- Ghostscript: Claude reportedly pivoted to reading the Git commit history, found a security-relevant commit, inferred what was vulnerable pre-fix, then looked for other call sites that didn’t have the same bounds-checking, and produced a proof-of-concept crash.
- OpenSC: Claude searched for function call patterns that are frequently vulnerable (e.g.,
strcat), found a risky concatenation chain with important preconditions, and Anthropic notes fuzzers studied that line infrequently because triggering it required many preconditions—whereas Claude reasoned toward the interesting fragment. - CGIF: Claude recognized a vulnerability tied to an assumption about compression behavior and articulated how a specific sequence could force compressed output to exceed expected size, leading to overflow. Anthropic frames this as requiring conceptual understanding of the format and algorithm, not just line coverage.
These examples are doing two things at once:
- Showing “Claude can find bugs.”
- Showing “Claude can navigate the search space in a way that looks less like brute force and more like research.”
That’s why defenders get excited. And why investors start running scary math on subscription multiples.
Dual-Use: The Reason This Is a Research Preview, Not a Victory Lap
Anthropic is explicit: the same capabilities that help defenders can help attackers exploit vulnerabilities.
In the “0-Days” write-up, Anthropic describes safeguards work including “probes” to detect certain harms at scale and the possibility of real-time intervention (including blocking traffic detected as malicious), while acknowledging it may create friction for legitimate research and defensive work.
This is the real strategic tension of AI security tooling:
- If you make it too easy to use, you risk enabling abuse.
- If you lock it down too hard, defenders don’t get the benefit.
- If you ship it broadly without careful controls, you may accidentally accelerate the exact problem you’re trying to solve.
So the cautious release posture isn’t just PR. It’s risk management.
The Stock Drop: What’s Verified vs. What’s Not
What’s verified
Multiple reports described a sharp selloff in cybersecurity names after the news. Bloomberg’s summary includes specific moves: CrowdStrike -8%, Cloudflare -8.1%, Zscaler -5.5%, SailPoint -9.4%, Okta -9.2%, and Global X Cybersecurity ETF -4.9%, closing at its lowest since November 2023.
What I could not verify from reputable sources
I could not find a reputable source confirming the specific claim that “$10B was wiped out in one hour” as stated. (It may be a rough estimate someone calculated by summing market-cap moves, but I didn’t see a mainstream outlet clearly reporting that number in the sources I reviewed.)
If you want to keep that line in your post anyway, the clean, non-hallucinatory way to write it is:
“Some market commentators claimed the selloff erased roughly $10B in value in a short window, though I haven’t seen a major outlet publish that exact figure.”
That preserves the vibe without asserting an unverified number as fact.
Did Anthropic “End Cybersecurity Subscriptions”?
No. Not literally—and not even close in the operational sense.
But the phrase is capturing something real: investors briefly priced in the possibility that AI makes certain security workflows dramatically cheaper.
Here’s the difference:
What Claude Code Security targets
Claude Code Security, as described by Anthropic, is aimed at finding and fixing vulnerabilities in code—especially subtle, context-dependent issues that rule-based tools miss—by reasoning across the codebase and suggesting patches for review.
That is closest to the “shift-left” universe:
- secure code review
- vulnerability discovery
- remediation suggestions
- backlog reduction in AppSec
What it does not replace
A huge chunk of cybersecurity spend has nothing to do with “find a bug in the codebase” and everything to do with:
- identity and access control
- endpoint detection and response
- incident response and forensics
- data loss prevention
- SIEM/SOAR workflows
- runtime protection and monitoring
- configuration drift and cloud posture
- third-party/vendor risk
Even within AppSec: finding a bug is not the same as shipping a safe fix at scale. Real remediation involves:
- patch review
- regression testing
- rollout management
- verifying exploitability in your environment
- prioritizing against active threats
- coordinating disclosure (especially for open-source dependencies)
Anthropic’s own materials emphasize human approval and acknowledge complexity and nuance.
So what’s the real meaning of the “ended subscriptions” line?
It’s shorthand for: “A big slice of recurring spend is justified by labor scarcity. If AI multiplies labor, budgets get renegotiated.”
That doesn’t mean “security goes away.” It means the value migrates.
The Real Story: AI Is Turning Security Work Into a Throughput Game
Cybersecurity has always been constrained by throughput:
- too much code
- too many dependencies
- too many CVEs
- too many alerts
- not enough qualified humans
Anthropic is explicitly building for that mismatch: “too many vulnerabilities and not enough people,” and the limitations of pattern-based tools in catching complex issues.
Claude Code Security is a bet that the new baseline is:
- AI continuously scans and reasons about codebases
- AI proposes fixes with confidence/severity metadata
- Humans focus on high-leverage judgment calls
- Patch cycles compress
- The “window of exposure” shrinks
If that loop becomes normal, it doesn’t eliminate security spend. It changes what you pay for.
Why Wall Street Panicked Anyway
Market selloffs often have a simple shape:
- A credible new capability appears
- Investors map it to revenue line items
- They sell first, ask questions later
From a distance, it’s easy to see the narrative investors latched onto:
- AI can “review entire codebases like a human expert” (Fortune’s phrasing)
- It self-checks, rates severity, suggests fixes
- It found hundreds of high-severity issues in open source that humans missed
- Therefore: some “security review” products are at risk of being commoditized or bundled into an AI platform
This is the “bundle” fear: if a general AI platform starts doing something that a specialized SaaS charged you for, the specialized SaaS either:
- moves upmarket into harder problems,
- becomes a layer within the platform,
- or competes on trust, workflow, and integrations.
In the short run, investors don’t wait to see which outcome happens.
The Most Important Detail Most Hot Takes Missed: “Validated” and “Human-Reviewed”
There’s a quiet but huge credibility signal in Anthropic’s write-up: it repeatedly emphasizes steps designed to prevent dumping low-quality AI output on maintainers and security teams.
- “Validated findings” appear in a dashboard.
- Claude attempts to prove/disprove its own findings.
- Nothing is applied without approval.
- For the 0-day effort, they validated bugs extensively before reporting and brought in external human researchers as volume grew.
That’s the opposite of “AI replaces security engineers.” It’s “AI becomes the world’s most tireless junior researcher—while humans remain accountable.”
If Claude Code Security actually holds that line in practice (low false positives, useful patches, responsible disclosure), then the long-term impact is likely bigger than a quick stock wobble—because the bottleneck moves.
Where This Could Genuinely Disrupt (Sooner Than People Think)
If we take Anthropic’s claims seriously, here are the categories most exposed—not because they become useless, but because they become less defensible as standalone subscription products:
1) Pure pattern-matching security scanning
If your product is mostly rules and signatures, and a general model can reason across codebases and catch issues you miss, you’re pressured to differentiate via workflow, compliance, reporting, and integrations.
2) Parts of “manual” secure code review
If a model can do first-pass reasoning, identify candidate issues, and generate patch suggestions, then the human review becomes about:
- verification
- exploitability
- architecture decisions
- risk acceptance
- deployment discipline
Humans still matter. But the time distribution changes.
3) Some pentest and audit workflows
Not all. But anything that was essentially “find obvious issues and write them up” gets squeezed.
4) Open-source vulnerability discovery as a scarce service
Anthropic is explicitly targeting open source first because vulnerabilities there “ripple across the internet,” and because many projects are maintained by small teams without dedicated security resources.
If AI can repeatedly surface high-severity issues in open source and assist in patching, the ecosystem changes.
Where This Probably Won’t Replace Spending (But Will Change It)
Even if Claude Code Security is fantastic, defenders still have a reality:
- many breaches come from misconfigurations, credential theft, phishing, social engineering, exposed services, and supply-chain compromises
- runtime detection and response is not optional for serious orgs
- compliance and reporting requirements remain
- incident response is still incident response
So the likely future isn’t “security budgets vanish.” It’s:
- AppSec becomes faster
- fix rates improve
- baseline hygiene rises
- attackers also speed up
- defenders race to shorten exposure windows
Anthropic itself points to this arms-race dynamic: attackers will use AI to find weaknesses faster than ever, so defenders need to move quickly to find and patch first.
Why the “Not a Product Launch” Framing Exists (and Why It’s Smart)
You can call this a product, because it is: Fortune calls it “Anthropic’s first product” aimed at this use case.
Anthropic calls it a “capability” and stresses “limited research preview.”
That difference is deliberate.
A big public GA launch invites:
- huge demand
- more adversarial use
- pressure to overpromise
- security researchers stress-testing it in public (for better and worse)
A research preview invites:
- controlled usage
- feedback loops
- gradual hardening
- time to build misuse detection and enforcement
Given the dual-use stakes, “preview first” is the rational move.
A Practical Playbook: How Security Teams Should Think About This (Right Now)
If you run AppSec or engineering security, Claude Code Security is not magic—but it’s worth a serious evaluation. Here’s a practical way to approach it without getting hypnotized:
1) Start with “where do we bleed time?”
Pick one or two problem areas:
- vulnerability backlog triage
- internal libraries with recurring issues
- legacy code with low test coverage
- high-risk parsers / file-handling components
- authentication and authorization surfaces
2) Define success in operational terms
Not “the AI is smart,” but:
- time-to-triage reduced
- false positives manageable
- patch suggestions usable
- severity rating aligns with human judgment
- measurable reduction in unresolved critical findings
3) Keep the human approval gate sacred
Anthropic’s own posture assumes humans approve changes.
Treat that as policy, not a feature toggle.
4) Pair it with your existing tools, don’t replace them on day one
The fastest wins usually come from stacking:
- your existing scanners for broad coverage
- AI reasoning for “weird” context-dependent issues
- humans for verification and deployment discipline
5) Think about disclosure workflows
If you maintain open-source projects, Anthropic explicitly encourages maintainers to apply for expedited access.
If you ship products, be ready for an era where vulnerabilities are found faster—by everyone.
The Bigger Picture: “AI-Discovered 0-Days” Becomes Normal
Anthropic’s 0-day write-up ends with a line that should make every engineering leader blink: models can add real value on top of existing discovery tools, but safeguards are essential due to dual-use risk.
That’s the new world:
- Vulnerability discovery speed increases
- Defensive scanning becomes more continuous
- Patch development gets partially automated
- The advantage shifts to teams with the best “find → verify → fix → ship” loop
In that world, the moat isn’t “we have a scanner.”
The moat is “we have the fastest secure delivery pipeline.”
So… What Happened Today?
On February 20, 2026:
- Anthropic announced Claude Code Security, a limited research preview built into Claude Code web, meant for defenders, with human approval gates and verification steps.
- Anthropic’s research materials claim 500+ validated high-severity vulnerabilities found in open-source codebases (with patches landing and disclosure underway), including issues that persisted for decades.
- Cybersecurity stocks sold off sharply, consistent with the narrative that AI could compress parts of the security tooling market.
- Some viral claims (like “$10B wiped out in one hour”) are floating around, but I did not see that exact figure confirmed by a major outlet in the sources reviewed.
The Takeaway
This isn’t “cybersecurity is over.”
It’s something more specific—and more disruptive:
Security work is turning into software throughput, and AI is about to crank the throughput knob.
Tools that sell “we help you find issues” will need to prove:
- they find more issues,
- with less noise,
- and they integrate into the end-to-end workflow of remediation and governance.
And for every security vendor that’s threatened, there’s another that will benefit—because if AI makes it easier to find vulnerabilities, it also makes it easier to prove you need stronger controls, better pipelines, and better operational response.
Security doesn’t get smaller.
It gets faster.
Sources (copy/paste links into WordPress)
Anthropic announcement (Feb 20, 2026): https://www.anthropic.com/news/claude-code-security
Anthropic Frontier Red Team — “0-Days” (2026): https://red.anthropic.com/2026/zero-days/
Fortune (Feb 20, 2026): https://fortune.com/2026/02/20/exclusive-anthropic-rolls-out-ai-tool-that-can-hunt-software-bugs-on-its-own-including-the-most-dangerous-ones-humans-miss/
Bloomberg (Feb 20, 2026): https://www.bloomberg.com/news/articles/2026-02-20/cyber-stocks-slide-as-anthropic-unveils-claude-code-security
If you want, I can also rewrite this into your house style (more “Kingy AI voice,” punchier hooks, more rhetorical cadence, tighter sections) without adding any unverified facts—just restructuring and sharpening what’s already here.
Re-write so the links are included in the article like a normal WordPress articleThought for 58s
Anthropic Didn’t “End Cybersecurity Subscriptions”… But Claude Code Security Just Made Investors Flinch
On February 20, 2026, Anthropic published a low-key post that triggered a very loud market reaction: Claude Code Security, a new capability built into Claude Code on the web, is now available in a limited research preview. It scans codebases for security vulnerabilities, proposes targeted patches, and routes everything through a verification flow designed to reduce false positives—with humans approving every change. (Anthropic announcement)
Within hours, cybersecurity stocks sold off hard. Bloomberg reported CrowdStrike (-8%), Cloudflare (-8.1%), Zscaler (-5.5%), SailPoint (-9.4%), and Okta (-9.2%), while the Global X Cybersecurity ETF fell 4.9% and closed at its lowest level since November 2023. (Bloomberg)
That’s how you get the viral headline energy: “subscriptions are over” and “$10B wiped out in an hour.” The problem is… the literal version of that story isn’t what Anthropic actually claimed, and the “$10B in one hour” figure isn’t something I’ve seen confirmed directly by a major outlet.
So let’s do this properly: what Anthropic actually released, what the research does (and doesn’t) prove, why markets panicked anyway, and what this means for the security industry if the tech holds up in the real world.
What Anthropic Actually Announced (No Hype Required)
Anthropic’s post is explicit about scope and posture:
- Claude Code Security is built into Claude Code on the web and is available in a limited research preview. (Anthropic)
- It scans codebases for vulnerabilities and suggests targeted patches for human review. (Anthropic)
- Each finding goes through a multi-stage verification process where Claude tries to prove or disprove its own result to filter false positives; findings get severity ratings, plus a confidence rating. (Anthropic)
- Nothing is applied without human approval—Claude proposes, developers decide. (Anthropic)
- Anthropic is opening preview access to Enterprise and Team customers, and it encourages open-source maintainers to apply for free, expedited access. (Anthropic)
There’s also a clear reason for the cautious rollout: dual-use risk. Anthropic notes that the same capabilities that help defenders find and fix vulnerabilities could help attackers exploit them. (Anthropic)
This is not Anthropic declaring it has “solved security.” It’s Anthropic saying: “The models are getting good at this. We’re previewing a defensive tool carefully.”
The Research That Spooked Everyone: “500+ High-Severity Vulnerabilities”
The thing that made people sit up wasn’t just “a scanner inside Claude Code.”
It was the accompanying claim: Anthropic’s Frontier Red Team used Claude Opus 4.6 to find over 500 high-severity vulnerabilities in production open-source codebases—some undetected for decades—while working through triage and responsible disclosure with maintainers. (Anthropic announcement)
Anthropic’s Frontier Red Team site goes even more direct:
“So far, we’ve found and validated more than 500 high-severity vulnerabilities.” (red.anthropic.com “0-Days”)
That “validated” word is doing a ton of work—because anyone who’s worked with open-source maintainers knows the pain: low-quality automated bug reports can become spam. Anthropic explicitly says it validated each bug extensively before reporting it, in part to avoid hallucinated findings. (red.anthropic.com)
And multiple reputable outlets echoed this thread:
- Fortune describes Claude Code Security as Anthropic’s first product aimed at helping security teams keep up with the volume of software bugs, while stressing that developers must review and approve changes. (Fortune)
- Axios reported earlier in February that Opus 4.6 found 500+ previously unknown high-severity security flaws in open-source libraries with little-to-no prompting and that each finding was validated by Anthropic or an outside security researcher. (Axios)
- CSO Online similarly reported the 500 figure and the emphasis on human verification to avoid false positives. (CSO Online)
This matters because it reframes what “AI for security” means. For years, a lot of AI security talk has been: “it helps triage alerts,” “it writes detection rules,” “it summarizes logs.”
This is different. This is: the model is operating like a vulnerability researcher—at scale.
Why This Isn’t Just Static Analysis With Better Marketing
Anthropic draws a sharp contrast between Claude Code Security and rule-based static analysis.
Static analysis typically matches code to known patterns: it can catch things like exposed secrets or outdated crypto, but it often misses complex bugs like business logic flaws or broken access control. Claude Code Security is framed as reading and reasoning about code like a human security researcher: understanding component interactions and tracing data flow through the application. (Anthropic)
Fortune uses similar language: instead of scanning for known problem patterns, Claude Code Security can review entire codebases “more like a human expert,” with self-checking, severity ratings, and suggested fixes—without auto-applying patches. (Fortune)
This is exactly where the market fear comes from:
- If a general AI system can do meaningful first-pass vulnerability discovery and propose fixes,
- then some portions of “security review” shift from scarce labor to scalable compute,
- and subscription products built mainly around “finding issues” get questioned.
Not because they become useless overnight—but because pricing power gets renegotiated.
“Bugs Humans Missed for Decades” — How Did Claude Find Them?
Anthropic’s 0-Days write-up is the most useful piece if you want to understand the mechanics instead of just repeating the headline.
The setup: a VM, standard tools, no custom harness
Anthropic says it put Claude in a virtual machine with access to current open-source projects and provided standard utilities and vulnerability analysis tools like debuggers and fuzzers—but no special instructions and no custom harness designed to teach it how to find issues. The idea was to test out-of-the-box capability. (red.anthropic.com)
To reduce hallucinations and false positives, it says it validated every bug extensively before reporting it and focused on memory corruption vulnerabilities early because they’re easier to validate (crashes, sanitizers, etc.). (red.anthropic.com)
Axios’ reporting is consistent: access to tools, no specialized knowledge or instructions, and validation by Anthropic or outside researchers. (Axios)
Concrete examples Anthropic highlighted
Anthropic’s write-up includes early examples from projects like Ghostscript, OpenSC, and CGIF, describing how Claude discovered vulnerabilities and how they were validated and patched with maintainers. (red.anthropic.com)
(Important note: Anthropic is not publishing a full list of 500+ vulnerabilities in public, presumably due to ongoing disclosure and obvious exploitation risk. That means we should treat “500+ validated” as a claim backed by Anthropic + reported by reputable outlets—but not something the public can independently audit line-by-line at this moment.)
Why It’s a Research Preview (and Why That’s Not a Small Detail)
This capability is inherently dual-use.
Anthropic says the same thing that helps defenders could help attackers exploit vulnerabilities, and it frames Claude Code Security as a way to push the advantage toward defenders—released carefully. (Anthropic)
CyberScoop’s coverage makes the operational angle more explicit: the feature is initially available to a limited number of enterprise and team customers, and the goal is to reduce large chunks of security review to a few clicks, with the user approving patching before deployment. It also notes restrictions on the signup page: testers must agree to use Claude Code Security only on code their company owns or holds rights to scan. (CyberScoop)
That posture—limited preview, explicit restrictions, human approval gate—is how you ship a capability that could otherwise become an exploit factory.
The Market Reaction: What’s Confirmed, What’s Not
Confirmed by Bloomberg: sharp selloff across major cyber names
Bloomberg’s summary of the day is clear: cybersecurity software companies “tumbled” after Anthropic introduced the feature, with multiple major names down mid-to-high single digits, and the cybersecurity ETF down 4.9%. (Bloomberg)
About that “$10B wiped out in one hour” line
I haven’t seen Bloomberg, Fortune, Axios, or Reuters publish that exact “$10B in one hour” figure in the sources above. It may be a rough estimate someone computed (summing market caps during an intraday move), but I can’t treat it as verified without a reputable outlet explicitly reporting it.
If you want to keep the flavor without inventing facts, a safe WordPress-friendly phrasing is:
“Some market commentary framed the selloff as billions in value erased quickly, though major outlets didn’t uniformly quantify it the same way.”
That keeps you honest and keeps your audience’s trust.
So Did Anthropic “End Cybersecurity Subscriptions”?
Literally? No.
But as a meme, it points at a real pressure wave: if AI can do high-quality vulnerability discovery and propose patches, certain categories of security tooling get forced to justify themselves differently.
Here’s the important distinction:
What Claude Code Security is clearly aimed at
Based on Anthropic’s description, the feature targets:
- secure code review / AppSec workflows
- vulnerability discovery in codebases
- patch suggestion + human approval
- reducing false positives via multi-stage verification
- severity + confidence metadata
That’s “shift-left” security: catching issues earlier, before runtime, before incidents.
What it does not replace (and likely won’t anytime soon)
Security spend also covers:
- identity and access management
- endpoint detection and response
- cloud posture management
- SIEM/SOAR pipelines
- runtime monitoring and incident response
- governance, compliance, and audit requirements
Claude Code Security doesn’t claim to replace those categories. It’s aimed at a specific bottleneck: too much code, too many vulnerabilities, not enough humans. (Anthropic)
So the “ended subscriptions” narrative is best read as:
AI is pressuring the parts of the security stack that monetize scarcity of human review time.
That’s not the whole industry. But it’s enough to rattle markets.
Why Investors Panicked Anyway (Even If the Tool Is Limited)
Markets don’t need a GA launch to reprice expectations. They just need a plausible path.
And Anthropic’s materials sketch a plausible path:
- Models are effective at finding “long-hidden bugs.” (Anthropic)
- Opus 4.6 found and validated 500+ high-severity vulnerabilities in open source. (red.anthropic.com)
- Anthropic expects a significant share of the world’s code will be scanned by AI in the near future. (Anthropic)
- The tool is being embedded into the developer workflow (Claude Code). (Anthropic)
That creates the bundling fear:
If a general AI platform includes a capability that overlaps with a standalone security product, the standalone product has to move up the stack—into workflow, governance, integrations, compliance, and runtime outcomes—or fight on price.
Even if that fear is exaggerated in the short run, it’s rational for investors to ask.
The Real Competitive Moat Moves Up a Level
If AI makes “finding bugs” cheaper and faster, the differentiator becomes less about detection and more about:
- verification workflows
- prioritization aligned to exploitability and business impact
- CI/CD integration
- policy enforcement and governance
- remediation rollout safety
- compliance reporting
- runtime detection + incident response
In other words: the moat becomes end-to-end security operations, not a single point tool.
Anthropic’s own positioning subtly reinforces this: it’s not “Claude finds bugs.” It’s “Claude finds bugs, verifies them, assigns severity, proposes patches, and keeps humans in control.” (Anthropic)
That’s workflow, not just detection.

What This Means for AppSec Teams (Practically, Not Philosophically)
If you run AppSec, this announcement isn’t a reason to throw out your stack. It’s a reason to test a new kind of teammate.
A grounded evaluation approach:
1) Pick one painful surface area
Examples:
- legacy parsers / file handling
- authentication + authorization logic
- internal libraries that keep reintroducing similar bugs
- dependency-heavy services where review is always behind
2) Define success as throughput + quality
Not “wow it’s smart,” but:
- fewer criticals stuck in backlog
- acceptable false-positive rates
- usable patch suggestions
- faster time-to-triage
- fewer “unknown unknowns” escaping into production
3) Keep humans as the approval gate
Anthropic explicitly frames this as human-reviewed and human-approved. Treat that as policy. (Anthropic)
4) Expect the attacker side to accelerate too
Anthropic explicitly warns that attackers will use AI to find weaknesses faster than ever. The defensive advantage is about moving quickly: find → patch → reduce exposure window. (Anthropic)
What This Means for Cybersecurity Vendors
This is the uncomfortable part.
If you sell:
- pattern-based scanning,
- “AI” that’s mostly UI over rules,
- or value that relies primarily on “we help you find issues,”
…you’re going to feel pressure.
But if you sell:
- remediation workflow,
- policy enforcement,
- compliance evidence,
- runtime outcomes,
- incident response capabilities,
…this may actually expand your TAM, because more vulnerabilities found faster can increase demand for remediation, governance, and operational safety.
CyberScoop also points out a nuance security practitioners will recognize: while model capabilities have improved, experienced human operators are still needed to manage higher-level threats and complex vulnerabilities in many organizations. (CyberScoop)
The future isn’t “humans vs AI.”
It’s “humans with AI vs humans without AI.”
The Most Important Detail People Skipped: “Validated” and “Human-Reviewed”
If you only remember one thing from all of this, make it this:
Anthropic is trying to solve the trust problem head-on.
- The red team write-up stresses validating every bug before reporting to avoid hallucinations and burdening maintainers. (red.anthropic.com)
- The product announcement stresses multi-stage verification, severity, confidence, and human approval. (Anthropic)
That’s how you make this category real.
If Claude Code Security produces high-signal findings and genuinely useful patches, it’s not “a scanner.” It’s a throughput engine for defense.
If it produces noise, it becomes just another tool that teams disable after two weeks.
Bottom Line
Anthropic did not declare cybersecurity “over.” It introduced a limited research preview that embeds vulnerability scanning and patch suggestions into a developer workflow—and backed it with research claiming 500+ validated high-severity vulnerabilities found in major open-source codebases. (Anthropic; red.anthropic.com)
Markets reacted sharply, with major cybersecurity stocks down significantly on the day. (Bloomberg)
The most reasonable interpretation is not “subscriptions ended.”
It’s this:
AI is getting good enough at vulnerability discovery that the pricing power of “manual review time” is being challenged—and the moat shifts toward end-to-end remediation, governance, and runtime outcomes.
Further reading (the same links, now embedded like a normal blog)
- Anthropic’s announcement: “Making frontier cybersecurity capabilities available to defenders” — Anthropic
- Frontier Red Team deep dive: “0-Days” — red.anthropic.com
- Market reaction: “Cyber Stocks Slide as Anthropic Unveils Claude Security Tool” — Bloomberg
- Product framing + context: Fortune exclusive — Fortune
- Early reporting on Opus 4.6 findings: Axios — Axios
- Trade coverage: CyberScoop — CyberScoop
If you want, I can also rewrite this again in a more “story-first” creator voice (stronger hook, tighter pacing, punchier subheads), while keeping the same verified facts and the same embedded links.