Security teams have been drowning for years: vulnerability backlogs keep growing, codebases keep expanding, and “more tools” hasn’t magically created more time. Anthropic’s Claude Code Security is a direct response to that reality: a new capability inside Claude Code on the web that scans codebases for vulnerabilities and proposes targeted patches for humans to review and approve.
This article breaks down everything that’s publicly documented about Claude Code Security: what it does, how it works (and how it differs from rule-based scanners), how to access it, who will use it, where it fits into existing security programs, and the pros/cons you should actually care about.
Along the way, I’ll also cover the closely related (and more widely available) feature Anthropic calls Automated Security Reviews in Claude Code—the /security-review command and a GitHub Action—because people will inevitably confuse these, and they’re meant to complement each other.
Table of contents
- What Claude Code Security is (and what it is not)
- Why it exists now: AI changes the economics of vulnerability discovery
- What it does: capabilities and outputs
- How it works under the hood (as described publicly)
- Access & availability: who can use it and how to get it
- The companion features:
/security-review+ GitHub Actions - Who will use it: roles, teams, and job functions
- Where it fits in a modern AppSec stack
- Data, privacy, and security posture (what Anthropic documents)
- Pros and cons: the real tradeoffs
- Implementation playbook: how to roll it out without chaos
- Practical FAQ + misconceptions
1) What Claude Code Security is (and what it is not)
Claude Code Security is a new capability built into Claude Code on the web. It scans a codebase for security vulnerabilities and suggests targeted software patches for human review—with the explicit intent of catching issues that traditional pattern-based approaches often miss.
A few key clarifications up front:
- It’s not “auto-fix everything.” Anthropic is explicit: nothing is applied without human approval. The system “identifies problems and suggests solutions,” but “developers always make the call.”
- It’s not generally available (yet). It’s in a limited research preview.
- It’s not the same thing as
/security-review. The/security-reviewcommand and GitHub Action are called Automated Security Reviews in Claude Code, and they’re available broadly to Claude Code users. Claude Code Security is the bigger “scan + dashboard + patch suggestions” capability currently in limited preview.
Primary sources to read first:
- Product page: https://claude.com/solutions/claude-code-security
- Announcement: https://www.anthropic.com/news/claude-code-security
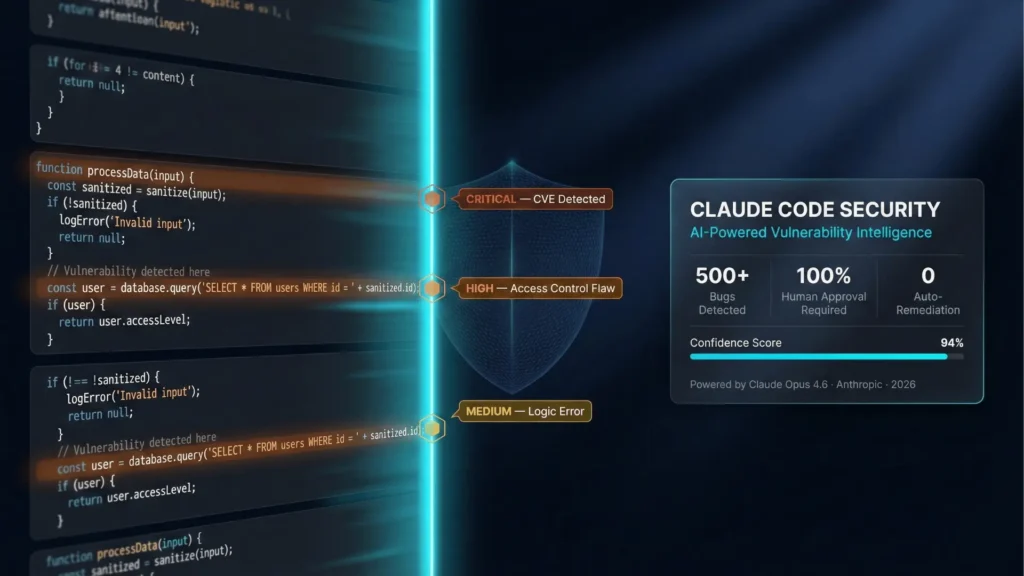
2) Why it exists now: AI changes the economics of vulnerability discovery
Anthropic’s public framing is blunt: defenders are outnumbered and backlogged, and rule-based scanners mostly catch what they already know how to catch. The hard stuff—the subtle, context-dependent vulnerabilities that get exploited in real incidents—has traditionally required scarce human expertise.
Anthropic argues AI is changing that calculus, pointing to internal “Frontier Red Team” work and collaborations aimed at defensive cybersecurity use:
- They describe over a year of research stress-testing cybersecurity abilities (including CTF participation and partnerships).
- They claim that using Claude Opus 4.6, their team found “over 500 vulnerabilities” across production open-source codebases, and they’re working through responsible disclosure.
- They also explicitly acknowledge the dual-use risk: the same capability that finds vulnerabilities can help attackers exploit them faster, which is why they position Claude Code Security as a defender-facing release with a limited preview.
Relevant “Frontier Red Team” context links Anthropic references:
- “Zero-days” research post (includes the “500+ vulnerabilities” claim): https://red.anthropic.com/2026/zero-days/
- Critical infrastructure defense research (PNNL partnership): https://red.anthropic.com/2026/critical-infrastructure-defense/
Whether you buy the broader thesis or not, the product direction is clear: treat security review like reasoning, not regex. And that leads to the next section.
3) What it does: capabilities and outputs
3.1 Scans codebases for vulnerabilities (beyond pattern matching)
Anthropic describes traditional static analysis as “typically rule-based,” good for common issues (exposed passwords, outdated crypto), but often missing complex vulnerabilities like business logic flaws or broken access control. Claude Code Security aims to read and reason about code “the way a human security researcher would”: understanding interactions, tracing data flows, and catching issues rule-based tools miss.
The product page also names categories it’s designed to catch, including:
- Memory corruption
- Injection flaws
- Authentication bypasses
- Complex logic errors
3.2 Produces suggested patches—but keeps humans in control
This is a major design choice: Claude Code Security doesn’t just flag a problem; it proposes a fix and puts that fix in front of humans to accept/reject.
Anthropic’s own wording: it “suggests targeted software patches for human review.”
3.3 Multi-stage verification, severity, and confidence rating
To fight false positives (the classic AppSec tax), Anthropic describes several layers:
- Multi-stage verification: Claude “re-examines each result,” attempting to prove or disprove its own findings and filter out false positives.
- Severity ratings: so teams can focus on what matters first.
- Confidence rating: because some vulnerabilities are “difficult to assess from source code alone,” so Claude provides a confidence rating per finding.
The product page also describes an “adversarial verification pass” that reviews suspected vulnerabilities and the corresponding patch to validate that:
- the vulnerability is real,
- the patch actually closes it, and
- the patch doesn’t introduce new issues.
3.4 A dashboard for triage + review
Anthropic says validated findings appear in a Claude Code Security dashboard, where teams can:
- review findings,
- inspect suggested patches,
- and approve fixes.
3.5 It’s built into Claude Code on the web (cloud execution model)
Claude Code Security lives inside Claude Code on the web, which runs tasks in Anthropic-managed virtual machines. The docs describe the basic flow: repo cloning, secure cloud environment setup, network configuration, task execution, and results pushed to a branch for PR creation.

4) How it works (publicly described)
Anthropic isn’t publishing a whitepaper with a full architecture diagram of Claude Code Security itself, but they do provide enough detail to understand the workflow philosophy:
4.1 “Human researcher” style reasoning
Instead of matching known patterns, Claude “reads and reasons about your code,” looking at component interactions and data flows.
4.2 Verification loops to reduce noise
The multi-stage verification + “prove/disprove itself” language is important because it suggests Claude Code Security is designed like a reasoning pipeline, not a single-pass analyzer.
4.3 Patch suggestions are first-class output
Claude Code Security isn’t just producing findings; it produces patches, then uses a verification pass to check the patch closes the vulnerability without introducing new issues.
4.4 Human approval is the control point
Anthropic emphasizes this repeatedly: no automatic application of fixes. The product is framed as “identify + suggest + prioritize,” with humans approving.
5) Access & availability: how to get Claude Code Security
5.1 It’s in limited research preview
Anthropic: “Claude Code Security… is now available in a limited research preview.”
5.2 Who it’s currently for
Anthropic says they’re opening the preview to:
- Enterprise and Team customers, and
- expedited access for maintainers of open-source repositories (they even encourage maintainers to apply for “free, expedited access”).
5.3 Where to apply
Anthropic links an “Apply for access here” form. (This is the one you included.)
- Apply page: https://claude.com/contact-sales/security
5.4 Important scope restrictions (don’t skip this)
On the application page, Anthropic includes restrictions that matter for policy and procurement conversations, including:
- you agree to use it only on codebases owned and controlled by your company, and
- you confirm you’re authorized by your security team to scan your code with Claude Code Security.
Those two bullets are telling: this is being treated as a security-sensitive capability, not “just another developer tool.”
6) The companion features: /security-review + GitHub Actions (Automated Security Reviews)
If Claude Code Security is the “big system,” Automated Security Reviews are the “daily driver” features many teams will deploy first.
Anthropic’s help center describes these as features that “help you identify and fix vulnerabilities in your code,” using:
/security-reviewin your terminal (on-demand), and- GitHub Actions (automatic PR reviews).
6.1 What these automated reviews detect (per Anthropic)
The help center lists common issues checked, including:
- SQL injection risks
- XSS vulnerabilities
- authentication flaws
- insecure data handling
- dependency vulnerabilities
6.2 Availability: these are widely available
Unlike Claude Code Security (limited preview), these features are available to “all Claude Code users,” including:
- individual paid plans (Pro/Max), and
- pay-as-you-go API Console accounts (including enterprises).
6.3 How to run /security-review
Anthropic’s documented workflow is simple:
- Open Claude Code in your project directory
- Run
/security-review - Claude analyzes and returns issues + explanations
- You can ask it to implement fixes
Doc: https://support.claude.com/en/articles/11932705-automated-security-reviews-in-claude-code
6.4 GitHub Actions: the official security review action
Anthropic maintains a GitHub repo:
https://github.com/anthropics/claude-code-security-review
The README emphasizes features like:
- diff-aware scanning (PRs: analyzes changed files)
- language-agnostic analysis
- PR comments with findings
- false-positive filtering
A very important security warning: the action is “not hardened against prompt injection attacks” and should only review trusted PRs. Anthropic recommends enabling GitHub’s “Require approval for all external contributors” so workflows only run after a maintainer reviews the PR.
Example workflow (from Anthropic’s README)
name: Security Reviewpermissions:
pull-requests: write
contents: readon:
pull_request:jobs:
security:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
with:
ref: ${{ github.event.pull_request.head.sha || github.sha }}
fetch-depth: 2
- uses: anthropics/claude-code-security-review@main
with:
comment-pr: true
claude-api-key: ${{ secrets.CLAUDE_API_KEY }}
7) Who will use Claude Code Security (jobs, roles, teams)
Claude Code Security is aimed at a very specific pain: security expertise bottlenecks. That means the “who” spans both security and engineering—because the workflow ends in patches that engineers must ship.
Primary users
- Application Security (AppSec) engineers: triage findings, validate exploitability, partner with dev teams on fixes.
- Product security engineers: focus on high-risk product surfaces, auth/privilege boundaries, multi-tenant issues.
- Security researchers / vulnerability management teams: run scans, prioritize, coordinate remediation across orgs.
- Security engineering managers: use the dashboard + ratings to drive prioritization and SLA discussions.
Secondary but inevitable users
- Backend and platform engineers: because suggested patches land in their repos and need review/approval.
- Tech leads: because they own risk decisions, timelines, and tradeoffs.
- DevOps / CI maintainers: for integrating automated review gates (especially the GitHub Action).
- Open-source maintainers: explicitly called out by Anthropic for expedited access.
“New” usage patterns it enables
Anthropic’s bigger claim is that Claude can surface subtle, context-dependent vulnerabilities that typically require skilled humans—and that it can reduce false positives via verification loops and confidence ratings.
If that holds in practice, the day-to-day impact is that AppSec teams spend more time confirming and fixing, less time sorting noisy scanner output.
8) Where it fits in an AppSec stack
Claude Code Security isn’t positioned as a replacement for everything. Think of it as a new layer that sits between:
- rule-based static analysis (fast, consistent, often noisy; great for known patterns), and
- human security review (slow, high-signal, limited capacity).
Anthropic explicitly contrasts its approach with “rule-based static analysis,” describing Claude’s strength as semantic reasoning about interactions and data flow.
A realistic integration looks like this:
Baseline program (typical mature org)
- existing SAST / dependency scanning / secret scanning
- code review + security champions
- pentest / red teaming
- vulnerability management + SLAs
Where Claude Code Security slots in
- Deep scan + prioritized findings + patch suggestions, particularly where your existing scanners are weak (logic, auth boundaries, complex flows).
- A triage surface (dashboard) that can become the “security backlog front door.”
Where /security-review slots in
- the developer workflow for pre-commit / pre-PR sanity checks, plus GitHub Actions for consistent PR review.
9) Data, privacy, and security posture (based on Anthropic’s docs)
When you’re scanning proprietary code, security posture isn’t a footnote—it’s the entire conversation with legal/procurement/security leadership.
9.1 Cloud execution model (Claude Code on the web)
Anthropic’s docs say:
- your repository is cloned to an Anthropic-managed virtual machine, and
- tasks execute in that environment.
They also describe network controls:
- cloud environments run behind a security proxy; outbound traffic goes through it for audit logging and abuse prevention.
And GitHub operations are handled through a dedicated proxy with scoped credentials, restricting risky operations (like pushing) to safer boundaries.
9.2 What data is sent and how it’s handled (Claude Code docs)
Anthropic’s “Data usage” doc states for local Claude Code:
- data sent includes all user prompts and model outputs,
- it’s encrypted in transit via TLS, and
- it is not encrypted at rest (per the doc).
For cloud execution:
- the repo is cloned to an isolated VM,
- GitHub credentials never enter the sandbox, and
- outbound network traffic goes through a security proxy.
Doc: https://code.claude.com/docs/en/data-usage
9.3 Security posture of agentic workflows (Claude Code security docs)
Anthropic’s Claude Code security doc emphasizes:
- strict permissioning by default
- sandboxing and write restrictions (write access confined to the project folder)
- guidance about prompt injection and risky commands like
curl/wgetbeing blocked by default
Doc: https://code.claude.com/docs/en/security
9.4 Why the GitHub Action warning matters
Anthropic explicitly warns the GitHub Action is not hardened against prompt injection and should only run on trusted PRs.
This is a practical reminder: if you deploy AI reviewers into CI without guardrails, attackers will try to feed them poison.
10) Pros and cons (the real tradeoffs)
Pros
1) It aims at the stuff rule-based tools miss
Anthropic’s core claim is semantic reasoning about interactions and data flow—catching subtle issues like business logic and access control failures.
2) Patch suggestions reduce time-to-remediation
Instead of “here’s a finding, good luck,” Claude Code Security proposes patches for review.
3) Verification loops + confidence ratings are designed to fight false positives
Multi-stage verification, prove/disprove passes, confidence ratings—these are explicit anti-noise design decisions.
4) Fits into existing workflows (PR-centric)
Claude Code on the web is built to end in a PR flow (review diff, iterate, create PR).
5) The “small” features are already useful (and widely available)
Even if you can’t access Claude Code Security yet, /security-review + the GitHub Action give you immediate value and let your team build muscle memory for AI-assisted security review.
Cons / limitations / risks
1) Limited preview means limited predictability
This is explicitly a “limited research preview.” Expect iteration, rough edges, and changing behavior.
2) Human review is mandatory—so capacity still matters
Claude can surface more issues, but your org still needs people to validate risk and approve patches. Anthropic is explicit that humans remain the decision point.
3) Data handling may be a blocker for some orgs
Anthropic’s own “Data usage” doc says prompts/outputs are sent, encrypted in transit, and (for local Claude Code) “not encrypted at rest.” Cloud execution includes proxies and sandboxing, but procurement teams will still ask hard questions.
4) CI automation has real prompt-injection risk
Anthropic explicitly warns the GitHub Action is not hardened against prompt injection and recommends guardrails.
5) No tool replaces security engineering judgment
Anthropic’s own documentation for automated security reviews says these features should “complement, not replace” existing practices and manual reviews.
11) Implementation playbook (how to roll this out without breaking trust)
If you’re leading security or platform engineering, here’s a practical rollout path that matches what’s publicly documented today:
Phase 1: Get immediate value with /security-review
- Update Claude Code as needed (
claude updateis mentioned by Anthropic) and use/security-reviewon meaningful changes. - Treat outputs as review prompts, not gospel. Keep your existing review gates.
Phase 2: Add the GitHub Action—carefully
- Use https://github.com/anthropics/claude-code-security-review for PR reviews.
- Implement the guardrail Anthropic recommends: require approval for external contributors so the workflow doesn’t run automatically on untrusted PRs.
- Start with one repo. Measure noise. Tune instructions (the action supports custom filtering instructions).
Phase 3: Apply for Claude Code Security (if you’re Team/Enterprise)
- Apply here: https://claude.com/contact-sales/security
- Be ready to show: internal authorization, code ownership, and security team approval.
Phase 4: Treat the dashboard like a vulnerability intake channel
- Use severity + confidence to drive triage rituals.
- Run regular “fix-it” cycles where suggested patches become PRs owned by engineering.
12) FAQ + common misconceptions
“Is Claude Code Security just SAST with AI branding?”
Anthropic’s claim is explicitly different: it’s meant to reason like a human researcher and catch complex issues rule-based SAST misses.
“Does it automatically commit fixes to my repo?”
Anthropic repeatedly says nothing is applied without human approval; suggested patches are for review.
“Can I use it if I’m an individual developer?”
Claude Code Security itself is in limited preview for Team/Enterprise (with expedited OSS maintainer access). But automated security reviews (/security-review + GitHub Actions) are available to all Claude Code users, including individual paid plans.
“Is the GitHub Action safe to run on any PR?”
Anthropic says no: it’s not hardened against prompt injection and should only review trusted PRs; they recommend requiring approval for external contributors.
Key sources (the ones worth bookmarking)
- Claude Code Security product page: https://claude.com/solutions/claude-code-security
- Anthropic announcement (Feb 20, 2026): https://www.anthropic.com/news/claude-code-security
- Apply for access: https://claude.com/contact-sales/security
- Automated Security Reviews help doc (
/security-review+ GitHub Actions): https://support.claude.com/en/articles/11932705-automated-security-reviews-in-claude-code - GitHub Action repo: https://github.com/anthropics/claude-code-security-review
- Claude Code on the web docs: https://code.claude.com/docs/en/claude-code-on-the-web
- Claude Code data usage: https://code.claude.com/docs/en/data-usage
- “Zero-days” research post: https://red.anthropic.com/2026/zero-days/
- Critical infrastructure defense research: https://red.anthropic.com/2026/critical-infrastructure-defense/
- (Video) “Find and fix security vulnerabilities with Claude”: https://youtu.be/sDpkV_iEnck







